Secruit makes it easy for security researchers to gather sub-domains for the target domain by integrating multiple tools into the platform's toolsuite.
The traditional way for sub-domain reconnaissance
DNS Dumpster is the passive way of doing the research.
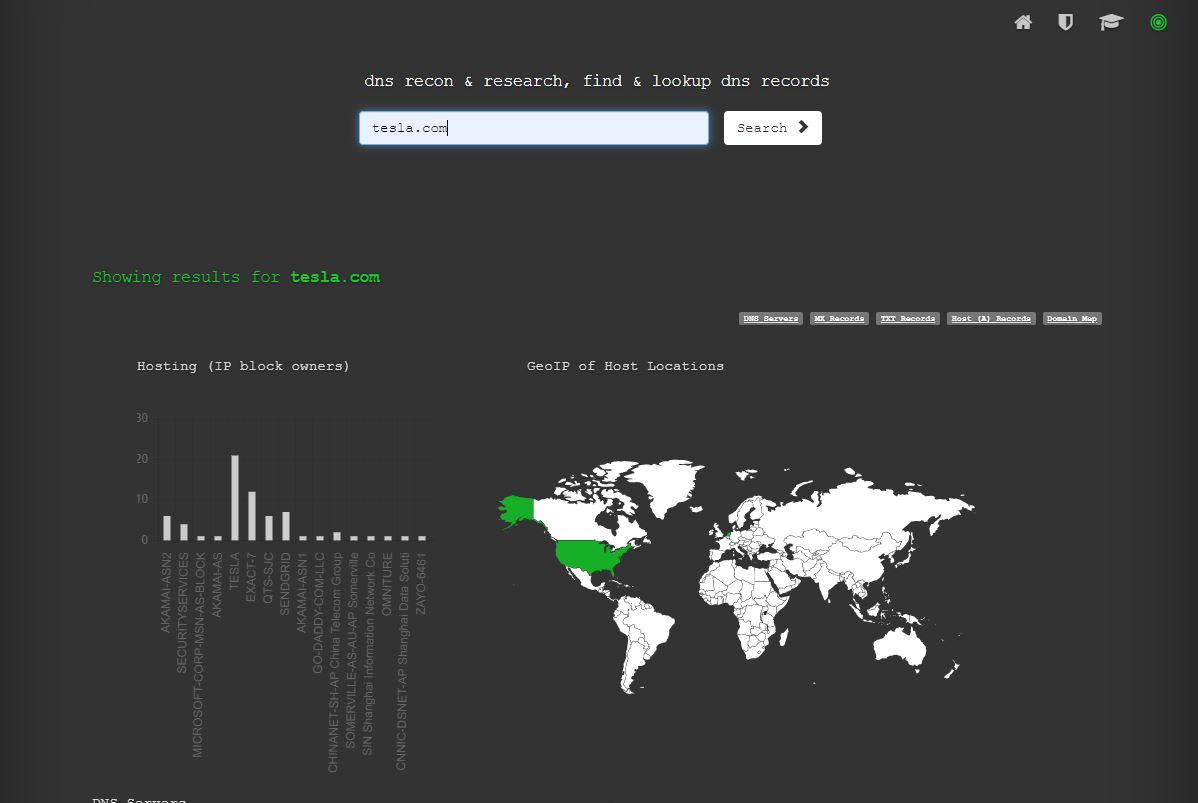
For example if you run DNS Dumpster on Tesla.com you get the following 60 subdomains.
Sub-domain reconnaissance with Contynuiti
Step 1: Select Target
Step 2: Add
Step 3: Review the list of "Assets" or sub-domains
<PLACEHOLDER>
As noted, Secruit reconnaisance delivers more accurate and complete sub-domain list. Once you click on any of the assets or sub-domains you will get all relevant information for that asset.
The primary benefit of Contynuiti's reconnaissance is a more complete assessment of the target, to get the best value in the security research.
To join the early rollout on the Contynuiti platform email [email protected] or contact us here.
![[object Object]](/lib_DSfaCgRdQhVLnhTY/jqivmg181attkmjb.png?w=268)